Collaboration Day
Friday, 15.09.2023, 9:30 – 17:00
by Project Teams

On the Collaboration Day, participants get the opportunity to work on interdisciplinary research and start-up projects. Teams of researchers and founders announce exciting tasks in advance, which are to be worked on together with the participants on Friday.
The teams will be supported by experts from dresden exists and guided by design thinking methods.
The description and collaboration tasks of the project teams can be found below.
Project 1: FusionSphere

At the Deutsche Telekom Professur für Kommunikationsnetze, cutting-edge research is not only carried out, but also applied. The demonstrator RoboSphere illustrates the potential of the combination of communication technology and robotics: Many robots in the smallest of spaces with optimally coordinated movement patterns open the door to the latest generation of production systems.
Problem
The RoboSphere impresses and enchants trade fair visitors, but these does not yet have the opportunity to look behind the veil. Up until now, simulation statuses, results and other “invisible” information have only been displayed on two screens. With the help of AR technology, one could overlay virtual information with the real RoboSphere. The viewer is thus offered an overwhelming picture of the amount of information hidden in the background. The RoboSphere as a multi-robot system would then not only be a hub for future production facilities, but also a hub between reality and the metaverse.
Task
The RoboSphere should be connected to AR technology, ideally Microsoft HoloLens. We create the basis for making virtual information accessible to viewers.
The application to be implemented is based on the movie Spider-Man 2 (2004). Inside the RoboSphere, a model of the sun is to be displayed and animated using the AR glasses.
The RoboSphere robots are then programmed to act like a fictitious containment field, preventing the virtual sun from expanding.
Required Skills
- AR glasses (HoloLens): Installation, data communication with Windows C#, additional software tools?
- Robotics: basic knowledge desired; Framework and software tools are available; you can propose your own trajectory planning algorithms
Project 2: smarobix

We enable the easy development and integration of efficient accelerated robotics systems. We provide a transparent, efficient, and intelligent integration of accelerators in robotic middlewares, thus building the infrastructure necessary to combine the skills of robotics experts and hardware acceleration experts to create optimized accelerated robotics solutions. Our solution brings the know-how on robotics, hardware accelerators, and adaptive software design for small, mid, and large-scale robotic systems with easy integration of all new and existing components.
Description of the demo
Having several building blocks (shown as individual demos of accelerated fpga applications), how can we build a demo to highlight the benefits of Smarobix
See picture attached for one of the demos
Task description for the workshop
Based on the introduction where we present our current status, tools and demos, we want you to come up with ides to show Smarobix in an exciting new demonstrator that combines all the bulding blocks that we presented.
Tentative Agenda
## 1. Introduction
1. Introduction to FPGAs in robotics
2. Challenges
3. Smarobix
1. Current state
2. Bulding block
3. Goals
## 2. Brainstorming
## 3. Hands-on developing
## 4. Presentation with outcome
Project 3: Enhancing Usability and Durability of Contacting Smart Textiles

The Institute of Textile Machinery and High Performance Material Technology (ITM) develop among other fibre-based sensor and actuator systems and integrated them into smart textiles, technical textiles and composite applications. Further tailored fibre-based textile-compatible sensors and actuator are a part of the research of the ITM. In addition to sensor and actuator development, the layout of systems and networks of sensors and actuators is also one of the research fields. They are used for sensory monitoring and actuation of textile-bases structures, e.g. smart textiles.
Short description of the topic
When connecting electronic components with smart textiles, there are still challenges in finding a permanently durable contact between rigid electronics and flexible textiles. The classic contacting solutions known from electrical engineering are unsuitable as temperatures during soldering are too high for textile materials, or crimping sleeves on the edges mechanically stress fine materials and ultimately destroy them. Therefore, electrically conductive adhesives and snap buttons are being resorted to. Both variants have their advantages and disadvantages. Electrically conductive adhesives allow direct connection of yarns to a wire, which is a great advantage. However, this comes with the disadvantage of a less mechanically stable contact and a negative impact to user-friendliness breaking after a short period of use. In contrast, the contacting variant via a snap button is mechanically stable, robust, and user-friendly. The contact can be disconnected and reconnected repeatedly to easily separate the electronics from the textile, e.g., for washing but, to ensure optimal contact, all yarn ends must be brought together in a large area to create an electrically conductive surface that can be contacted. Depending on the smart textile, however, oftentimes it is not possible to bring together all the individual components, for example, the five sensors in the CeTI glove, to form one surface, or the size of the smart textile does not even allow a contacting surface for a snap button. Alternative user-friendly and durable contracting solutions must therefore be found for smart textiles independent of the product’s size and design.
Previous knowledge for processing the topic
- Basic knowledge of textile engineering and smart textiles
- Basic knowledge of electrical engineering
- Use of a multimeter for checking the resistance of the contacting
- Creativity
- Fun tinkering and trying things out
Project 4: How can we identify and fight privacy risks in digital health?
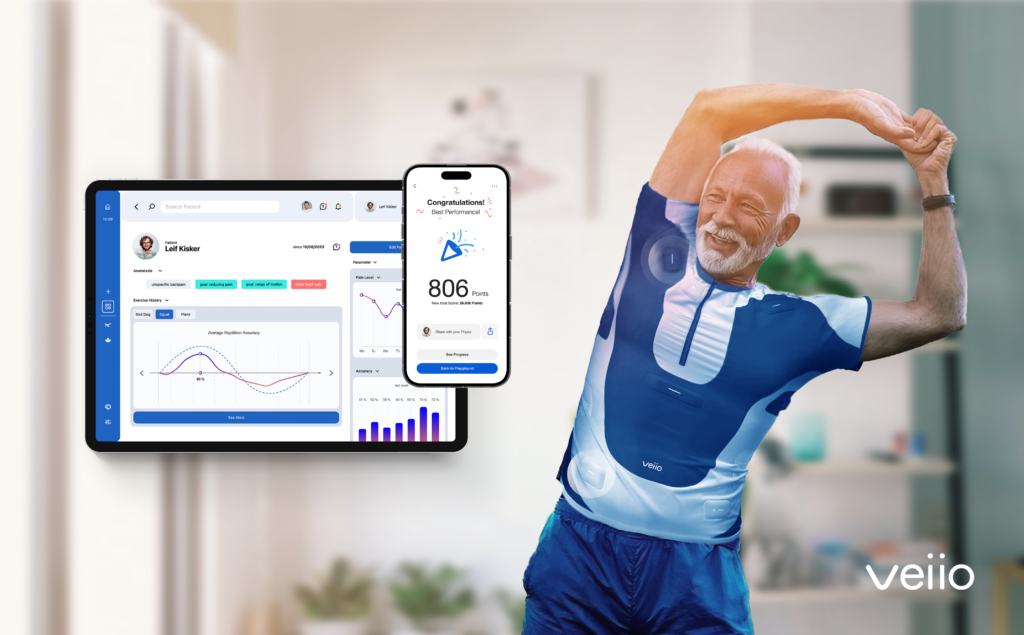
Almost two thirds of the German population complain of back pain, and one fifth of them are even affected by chronic, almost daily pain. AI-based cyber-physical systems such as the veiio shirt, which provide real-time haptic feedback during physiotherapy exercises at home, have the potential to improve treatment adherence and thus sustainable healing for back pain patients. A major hurdle for the adption of such systems are regulations and concerns about the privacy of those very sensitive biomedical data collected.
Framing this scenario, training machine learning models on mobile hardware is difficult because it requires large amounts of processing power and consumes a lot of energy. Therefore, offloading model training to the cloud is beneficial. However, this poses a privacy problem as the trained data has to leave the mobile device on which it was recorded. Thus, we need to thoroughly identify and counteract all the potential privacy threats presented by offloading different parts of the system further away from the user.
One portion of the data consists of the demographic and biometric data about the patient (age, gender, height, weight, etc), as well as the physiotherapist’s treatment plan. It is then followed by streams of data collected from IMU sensors during exercise sessions at home, as well as streams of feedback data back from the machine learning model.
The system contains 4 different machine learning components for pose estimation and feedback customization and the inference and/or training can be performed on one of the three locations: 1) the shirt hub 2) a user owned mobile device 3) cloud.
The goal of this exercise is to identify and suggest countermeasures for the potential privacy threats and concerns given its components and their potential locations. The participants will do this by following the Privacy Impact Assessment (PIA) CNIL framework, which includes identifying the system’s assets and processes, then assessing potential risks, and, finally, finding ways to evaluate and counteract these risks.
